Last week a security researcher who goes by the name of Adam performed a very detailed and easy to read analysis of a new ransomware called NanoLocker. At the time of his analysis there was only a brief write-up on Symantec's site that showed some basic information about the ransomware.
When he analyzed the ransomware, though, he found that it contained some interesting features including how it communicates with the Command & Control server and a flaw in the way it temporarily stores the AES key. This flaw can the be used to decrypt a victim's files in the right circumstances.
The NanoLocker Encryption Process
Thanks to the hashes posted by Adam I was able to get a sample of the ransomware and test it out on a virtual machine. This ransomware executable has a PDF icon that makes me think that it is probably distributed as an email attachment. Once executed, it will display a fake PDF error to make it seem like the PDF had a problem opening.
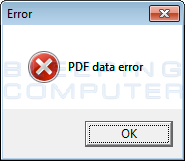
In reality, though, the program is now running silently in the background and scanning your drives for data to encrypt. When it finds a targeted data file it will encrypt it using AES encryption and then an add the filename and its path to the %LocalAppData%\lansrv.ini file. The file extensions targeted by NanoLocker are:
*.jpg, *.jpeg, *.tif, *.bmp, *.max, *.accdb, *.dbf, *.mdb, *.pdb, *.sql, *.*sav*, *.*spv*, *.*grle*, *.*mlx*, *.*game*, *.*slot*, *.dwg, *.dxf, *.cpp, *.php, *.asp, *.java, *.jar, *.class, *.aaf, *.aep, *.aepx, *.plb, *.prel, *.prproj, *.aet, *.ppj, *.psd, *.indd, *.indl, *.indt, *.indb, *.inx, *.idml, *.pmd, *.xqx, *.eps, *.svg, *.swf, *.fla, *.doc, *.dot, *.docx, *.docm, *.dotx, *.dotm, *.docb, *.rtf, *.wpd, *.wps, *.msg, *.pdf, *.xls, *.xlt, *.xlm, *.xlsx, *.xlsm, *.xltx, *.xltm, *.xlsb, *.xla, *.xlam, *.xll, *.xlw, *.ppt, *.pot, *.pps, *.pptx, *.pptm, *.potx, *.potm, *.ppam, *.ppsx, *.ppsm, *.sldx, *.sldm, *.wav, *.aif, *.iff, *.mid, *.mpa, *.wma, *.avi, *.mov, *.mpeg, *.asf, *.asx, *.flv, *.mpg, *.wmv, *.vob, *.csv, *.efx, *.sdf, *.vcf, *.xml, *.crt, *.pem, *.cer, *.pfx, *.odt, *.ods, *.odp, *.odm, *.odb, *.odc, *.xlk, *.dxg, *.pst, *.mdf, *.cdr, *.arw, *.dng, *.rar, *.zip, *.srf, *.bay, *.crw, *.dcr, *.kdc, *.erf, *.mef, *.mrw, *.nef, *.nrw, *.orf, *.raf, *.raw, *.rwl, *.ptx, *.pef, *.srw, *.der
It should be noted that this extension list appears to be identical to the list targeted by Ransom32.
When it has finished encrypting your data, the program will continue running but will now display a ransom note and fields that can be used to enter the key and decrypt your files.
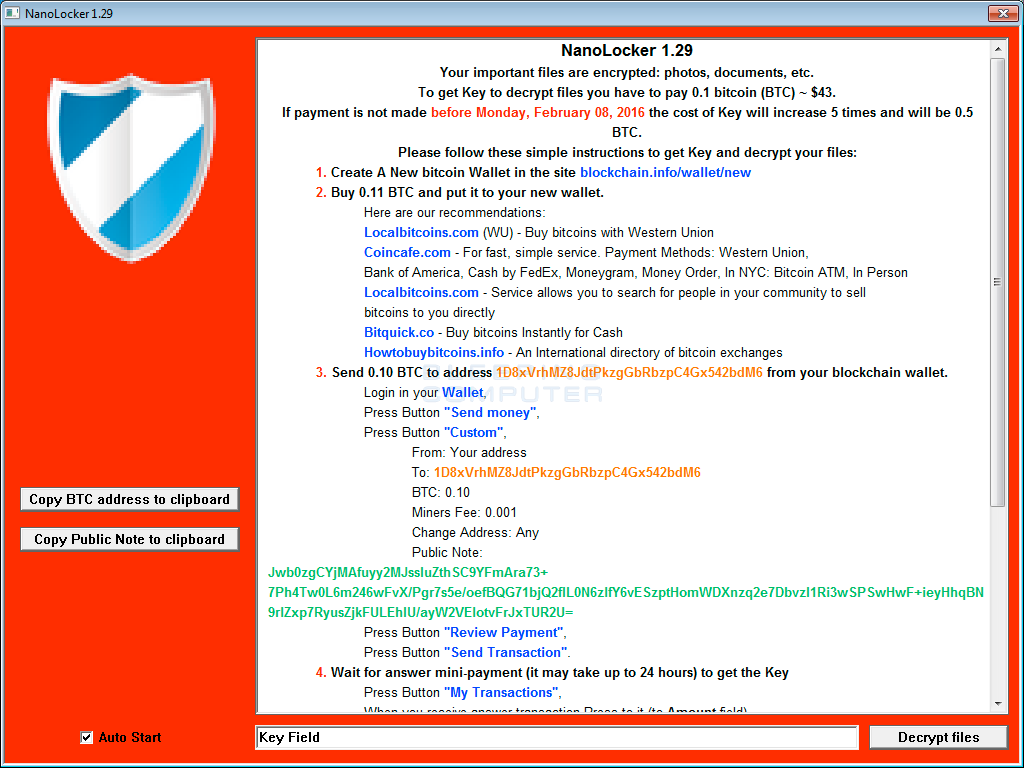
This ransom screen will contain instructions on how you can pay the ransom note. When a key is received (more info below), you can paste the key in the Key Field and decrypt files directly from the application.
According to Adam, this ransomware communicates with the Command & Control Server using ICMP packets. This is a innovative method and the first time to my knowledge of a ransomware using ICMP to communicate with the C2.
Another interesting feature of this Ransomware is that it gives you the ability to disable the autostart for the executable so the ransomware no longer starts when you login.
The Payment Process
Unlike most other ransomware, NanoLocker only requests .1 bitcoins to get your files back, which equates to about 43 USD. Due to the low distribution of this ransomware and the small ransom amount, this release may have been a test run.
NanoLocker also uses an unique payment method and key retrieval when paying the ransom. When paying the ransom you are required to send a BASE64 encoded string in the Public Note field when you send the payment. This public note then gets attached to the bitcoin transaction and can be read by the malware developer. When the payment is received, the malware developer will then send back a micro-transaction that contains another Public Note that contains your decryption key.
A victim would then take this key and paste into the Key Field box in the program to decrypt their files.
NanoLocker's Key Storage Flaw
When NanoLocker encrypts a file it uses the symmetrical AES encryption algorithm, which means that the same key is used to both encrypt and decrypt a file. Unfortunately, when the ransomware is finished encrypting the files, it then encrypts this AES key with a master RSA public encryption key and stores it in the %LocalAppData%\lansrv.ini. In this final state, since the AES key is now encrypted, we cannot use it to decrypt a victim's files.
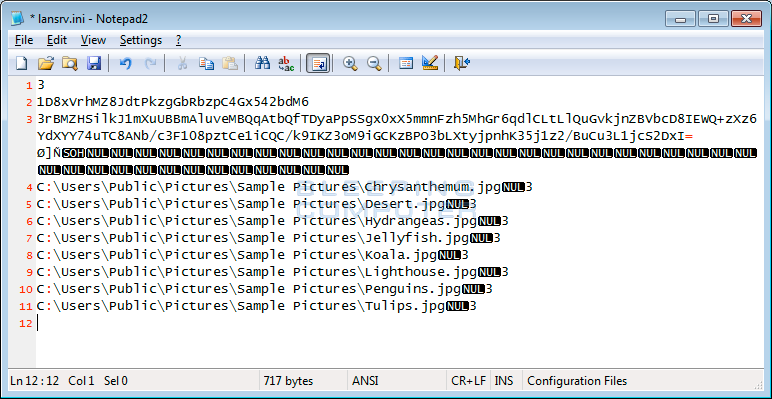
What Adam discovered, though, was that while NanoLocker is encrypting a victim's files, it stores the unencrypted AES key in the %LocalAppData%\lansrv.ini file. This was done so that if a victim turns off the computer before the encryption has finished, the ransomware can continue from where it left off when the user starts the computer again.
This transient key storage mechanism can, though, be exploited to our advantage. If a victim shuts down the computer or terminates the ransomware process before the infection has finished encrypting the computer, then they can retrieve the key from the %LocalAppData%\lansrv.ini file and use it to decrypt their files.
Decrypting NanoLocker
As already stated, there is no weakness in the encryption algorithm that allows us to decrypt NanoLocker encrypted files. Instead, a victim would have had to shutdown the computer or terminate the ransomware before it finished encrypting in order for us to retrieve the unencrypted encryption key. For those who were able to retrieve the key, Adam has created a decryptor that can import this key and decrypt the encrypted files.
Adam's decryptor needs to be run from the Windows command line and unfortunately can only decrypt one file at a time. For those who want to add more features to Adam's decryptor, he has posted the full source code on GitHub. A list of all encrypted files can be found in the %LocalAppData%\lansrv.ini file.
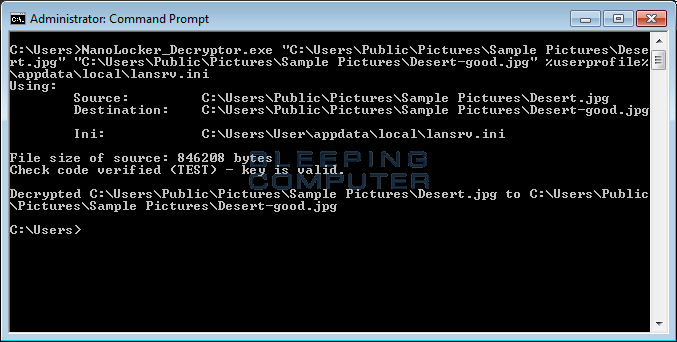
To use this decryptor, download it from here and save it to your desktop. From a command line execute the decryptor using this command line:
NanoLocker_Decryptor.exe [encrypted_file] [file_to_save_decrypted_version] [lansrv.ini_file]
A real example that shows how to use this decryptor would be:
NanoLocker_Decryptor.exe "C:\Users\Public\Pictures\Sample Pictures\Desert.jpg" "C:\Users\Public\Pictures\Sample Pictures\Desert-good.jpg" %userprofile%\appdata\local\lansrv.ini
Once you execute the command, the decryptor will make sure the key is valid and decrypt your file as shown below.
As already stated, this decryptor only decrypts one file at a time, so if you need to use it to decrypt entire folders, you would need to use a batch file or someone would need to add further features to the source code of this program. If you create a batch file, you could export the list of encrypted files from the %LocalAppData%\lansrv.ini file and then read that into a loop that decrypts each file.
Files associated with NanoLocker
C:\Users\User\AppData\Local\lansrv.exe
C:\Users\User\AppData\Local\lansrv.ini
C:\Users\User\Desktop\ATTENTION.RTF
Registry entries associated with NanoLocker
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\LanmanServer C:\Users\User\AppData\Local\lansrv.exe


Comments
karolisbar - 8 years ago
For future, test them on real machines, because not everything works properly on a VM.
ScathEnfys - 8 years ago
True, but it's not always possible to have a sacrificial machine on hand to test malware samples. Considering that this guy is Simi-anonymous I don't think we can expect him to necessary have all the tools a major company would have for this sort of thing.