LeChiffre is a ransomware that we have been seeing in our forums since June 2015, but have been unable to acquire a sample until recently. This is because the LeChiffre ransomware is not distributed via normal means such as Trojan downloads, exploit kits, or email, but rather by being manually installed in hacked servers. When the malware developers hack a server via remote desktop or terminal services, they manually run the executable to encrypt the data and then remove all traces of the program when they leave.
It wasn't until recently that Hasherezade of Malwarebytes was able to acquire a sample and perform an analysis of it. This analysis showed that the ransomware was not very sophisticated but rather a simple client that the malware developers would run on a hacked server to encrypt the data files and leave a ransom note.
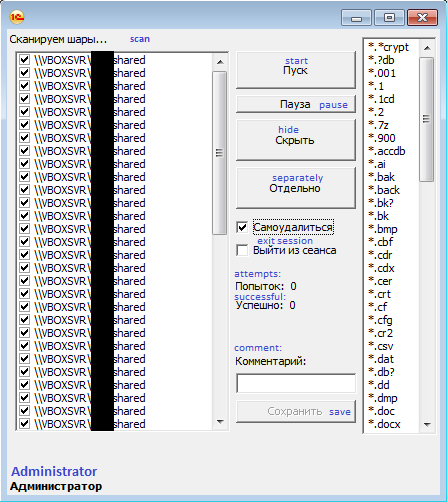
Once the hackers were done encrypting the drives, they would clean up behind themselves and wait for the payment to come in.
When the program encrypted a data file it would append the .lechiffre extension to the filename and generate a ransom note called _How to decrypt LeChiffre files.html in the encrypted file's folder. These ransom notes contain information about what happened to the victim's data and the decrypt.my.files@gmail.com email address that can be used to get payment instructions. An interesting offer in the ransom note is that if a victim does not need their files immediately, they can wait 6 months and get them back for free.
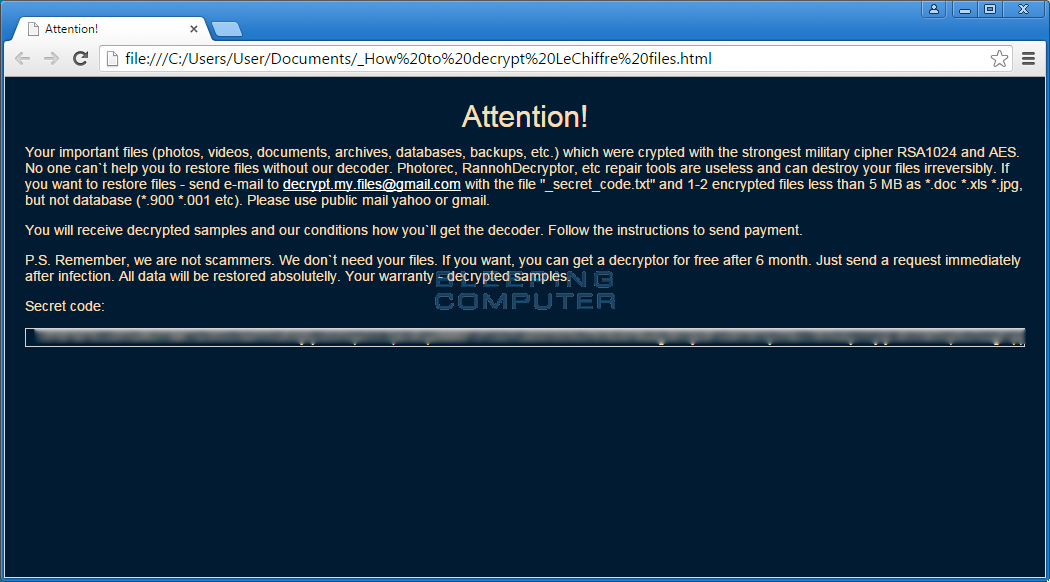
Hasherezade was gracious enough to share a sample with the security community and when Fabian Wosar of Emsisoft analyzed it he discovered a vulnerability that could allow him to build a free decryptor for it. More information about this vulnerability can be found in this post and instructions on how to use the decryptor can be found below.
LeChiffre Decrypted
If you are infected with the LeChiffre ransomware, simple download download decrypt_lechiffre.exe from the following link and save it on your desktop:
Decrypt LeChiffre Download
Once you have downloaded the executable, double-click on it to launch the program. When the program starts, you will be presented with a UAC prompt as shown below. Please click on Yes button to proceed.
You will then be presented with a license agreement that you must click on Yes to continue. You will now see the main LeChiffre Decrypter screen.
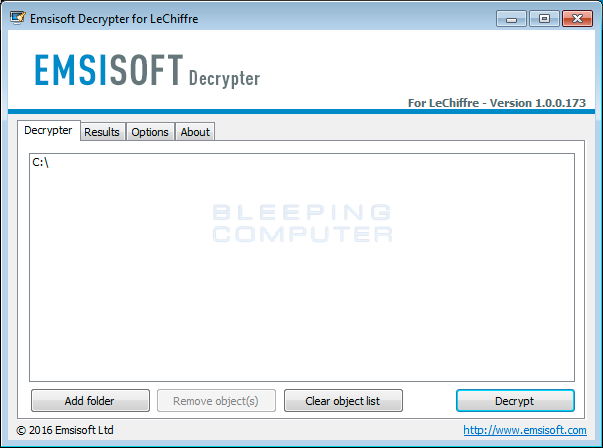
To decrypt the C:\ drive click on the Decrypt button. If there are other drives or folder you wish to decrypt that are not listed, you can click on the Add Folder button to add other folders that contain encrypted files. Once you have added all the folders you wish to decrypt, click on the Decrypt button to begin the decryption process. Once you click Decrypt, the LeChiffre Decrypter will decrypt all the encrypted files and display the decryption status in a results screen like the one below.
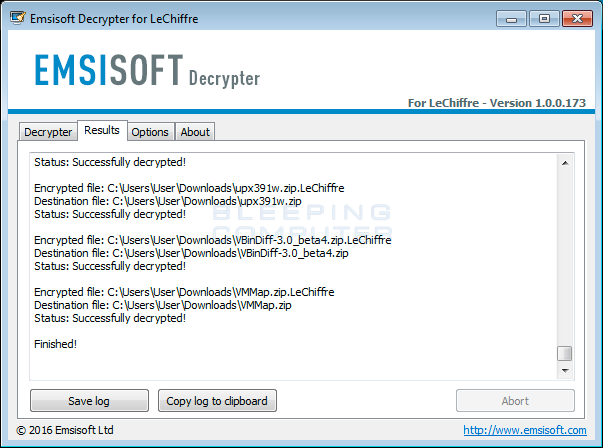
Most of your files should now be decrypted. If you need any help using this tool, you can ask in the LeChiffre Ransomware Support Topic.



Comments
GeoffTrowbridge - 8 years ago
Sadly, the utility doesn't work. It says it has decrypted the files, but they all still are corrupted and inaccessible.
PCLuis04 - 8 years ago
Same here. They turned back into regular PDF files but I get an error that they are unable to be opened.
samkan1 - 8 years ago
SAME ISSUE. WHAT DO WE DO? ANY IDEA? It seems like the decrypter was recognizing the encryption but when the document is decrypter it still does not open.
I have a lot of docs to decrypt.
ps. after decrypting .LeChiffre decrypted files...I got his again by another this time .LOL!.LeChiffre...this decryptor does not recognize the new extension on the document.
FGump - 8 years ago
03-15-2016 - Didn't work for me either and the section allowing to enter a key is disabled! No updates on this software or other versions since it's release. Looks like it's very difficult to get support on this!
SAGITARIUS - 8 years ago
Yes is not working at all.. the files are still damaged not matter what type of files are they.
Word of advice from me - the ZIP and RAR files can be repaired by WinRAR. Just open WinRAR and click on repair button after you select the file you want to repair in the WinRAR's file manager.
..the XLS and XLSX files I have repaired ( or most of them ) with OfficeRecovery 2013 Ultimate v13. This soft works and with other types of encrypted files.
rengrish - 8 years ago
Yes it not working for JPEG files .
Thalu - 7 years ago
It has a new Lechiffre version that does not work with this tool and none else from TrendMicro or Avira. The e-mail in the rescue file is: lechiffre@india.com lechiffre@mailchuck.com
Are there any updated tools for this virus?
thanks
werries87 - 7 years ago
New version also detected on one of our servers. I will upload some samples.
Smapppp - 7 years ago
I got the new version too. And the tool does not work. Are there any idea how to solve the problem?